
Vulnerability Identification
Proactively identify where your organisations products are vulnerable to attacker exploitation.
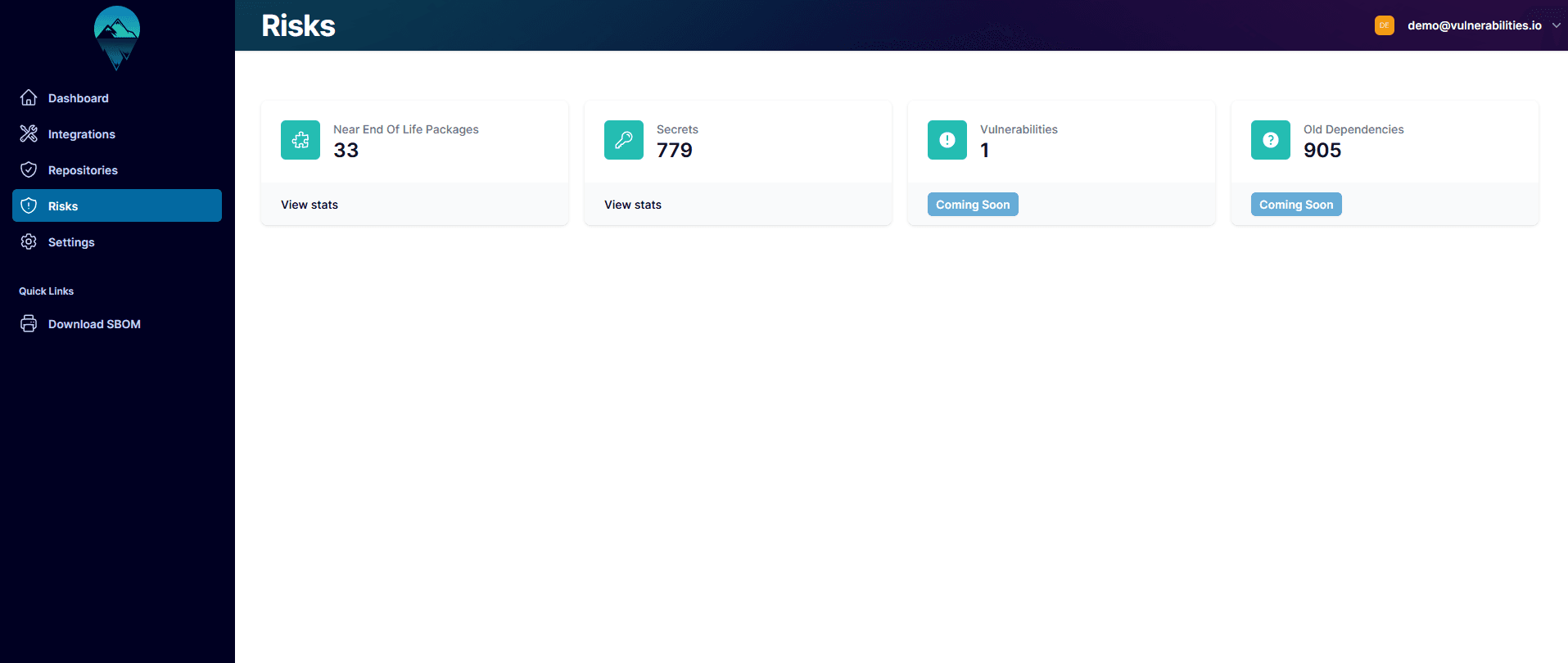
Vulnerability Identification
Don't leave yourself vulnerable to threats
Through utilisation of our comprehensive vulnerability database, vulnerabilities.io is able to determine where your projects, or the software they depend upon on, are at risk.
Measure your vulnerability risk picture over time to highlight areas of your stack that require focus.
Comprehensive coverage. Our platform integrates with all of your source control systems, get all of this information in one place and avoid the need for separate technology solutions.
Product reports to articulate your vulnerability posture, including as part of Software Bill Of Materials exports.
Avoid alert fatigue and save engineering time.
We'll only show you issues that really impact you.
